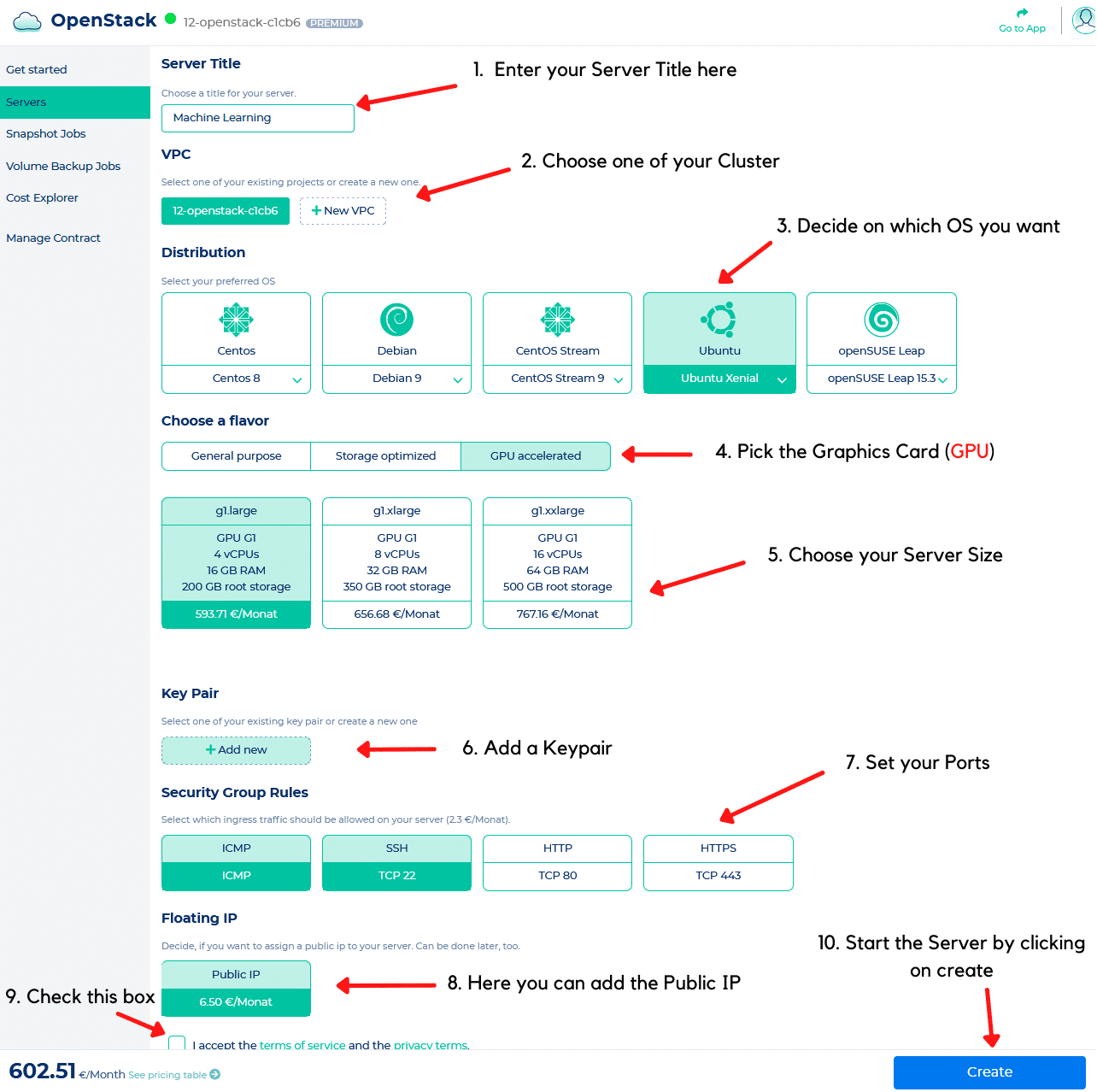
We’re starting the new year with a new integration for you! As announced last year, the integration of further products with NWS-ID will continue in 2023! From now on the NWS Cloud Services are integrated with NWS-ID.
What are the advantages of integrating our Cloud Services with NWS-ID?
Combining these two services makes your daily work easier, because now you can:
- use a single login for both interfaces (Customer Interface and Cloud Interface)
- effortless switch between OpenStack projects, in the Customer Interface, in the Cloud Interface (Horizon) and on the OpenStack CLI
- use two-factor authentication for your Cloud Services
- authorise your colleagues to access your OpenStack projects in the NWS-ID group management
How can you use the Cloud Interface with NWS-ID?
Select NWS-ID at cloud.netways.de, log in and you’re done – simple as that! If you’re not an admin in your organization, they must authorize your NWS-ID. This happens as usual in the user group management in the customer interface.
How do I use the OpenStack-CLI with NWS ID?
As usual, you need an OpenStack Environment File. You can find a version adapted for NWS-ID under Get Started in your OpenStack project in the Customer Interface or in our NWS Docs.
If you’re a member of several OpenStack projects, you can easily switch between them. Simply source the OpenStack Environment File again to get a selection.
Don’t have the official OpenStack CLI client yet? No problem – you can get help in the NWS Docs!
What happens to the existing login?
The existing login can still be used, e.g. in your scripts or tools like Terraform. The password can be changed as usual on cloud.netways.de or via the OpenStack CLI.
What’s coming next?
For a more effortless access, we will gradually integrate our portfolio with NWS-ID. We are already playing with kubelogin and we are looking for a simple Vault SSH integration to extend the reach of your NWS-ID to your OpenStack Cloud Servers.
The same procedure as last year still applies. Please give us a little time to implement the integrations and we will of course come back to you as soon as possible! If you have any questions along the way, please feel free to contact us – we’re always there to help answer any open questions.