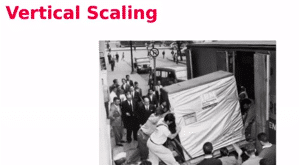
Der heute erreichte Grad der Virtualisierung erlaubt es, nahezu ganze Rechenzentren und ihre Netzinfrastruktur virtuell abzubilden. Dazu bedarf es eines Infrastructure-as-Code-Werkzeugs wie Terraform, das sich dem Multicloud-Management verschrieben hat. Terraform stellt Rechenzentrumsressourcen unterschiedlicher Cloud-Provider bereit – bei Bedarf auch für andere Werkzeuge.

Wir haben die Terraform Schulung in drei Versionen im Programm, mit Fokus auf OpenStack, AWS oder Azure. Darum geht’s bei allen dreien: Mit der aktuellen Version von Terraform und seiner Konfigurationssprache HCL (Hashicorp Configuration Language) in Version 0.12 hat sich das Vorgehen zur Automatisierung von Cloud Infrastruktur weiterentwickelt. Unsere Terraform Schulung zeigt, wie Infrastruktur mit der Terraform eigenen DSL (HCL, Hashicorp Configuration Language) idempotent realisiert wird. Neben der Theorie mit vielen Beispielen beinhalten die Fortbildungen praktische Übungen anhand von OpenStack, AWS oder Azure. Ebenfalls erfolgt eine kurze Einführung in cloud-init, um weitere Software zu installieren und zu konfigurieren.
Die kommenden Terraform Schulungstermine
- Terraform mit AWS Training in Nürnberg, 19. – 20. Oktober 2021
- Terraform mit Azure Training in Nürnberg, 28. – 29. Oktober 2021
Melde Dich jetzt an und sichere Dir Deinen Platz!
Die genauen Inhalte, Voraussetzungen und alles weitere Wissenwerte erfährst Du auf unserer NETWAYS Trainings-Seite zur Terraform Schulung.
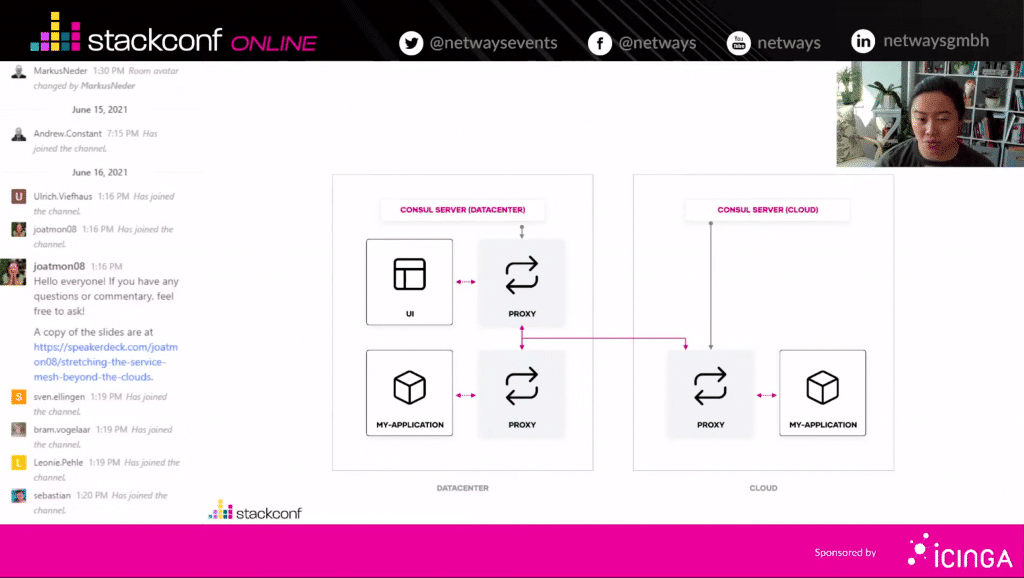

 So lässt sich das OpenStack Projekt bequem und übersichtlich über unser Dashboard zusammenstellen und einrichten. Der Punkt der Übersichtlichkeit führt mich auch gleich zu einem weiteren wichtigen Vorteil unseres OpenStack Angebots: Bezüglich der Kosten können wir ein maximales Maß an Transparenz bereitstellen. Es gibt keine undurchsichtigen Pauschalen und Gesamtpakete. Alle verwendeten Ressourcen werden stundengenau abgerechnet. Über unseren Cost Explorer siehst Du die für den Monat bereits entstanden Kosten und bekommst anhand der aktuell genutzten Ressourcen auch gleich eine Hochrechnung über die voraussichtliche Summe am Monatsende. Man hat die Kosten also zu jeder Zeit im Blick und kann im Bedarfsfall sofort reagieren. Das liegt auch daran, dass es keinerlei Vertragslaufzeiten gibt. Wird eine VM nicht mehr benötigt, kann man diese umgehend runterfahren. Am Monatsende zahlst Du dann nur den Betrag, der bis zu der Abschaltung entstanden ist. Das gibt Dir absolute Flexibilität in beide Richtungen – Du kannst schnell wachsen und, wenn nötig, Dein Setup auch direkt verkleinern.
So lässt sich das OpenStack Projekt bequem und übersichtlich über unser Dashboard zusammenstellen und einrichten. Der Punkt der Übersichtlichkeit führt mich auch gleich zu einem weiteren wichtigen Vorteil unseres OpenStack Angebots: Bezüglich der Kosten können wir ein maximales Maß an Transparenz bereitstellen. Es gibt keine undurchsichtigen Pauschalen und Gesamtpakete. Alle verwendeten Ressourcen werden stundengenau abgerechnet. Über unseren Cost Explorer siehst Du die für den Monat bereits entstanden Kosten und bekommst anhand der aktuell genutzten Ressourcen auch gleich eine Hochrechnung über die voraussichtliche Summe am Monatsende. Man hat die Kosten also zu jeder Zeit im Blick und kann im Bedarfsfall sofort reagieren. Das liegt auch daran, dass es keinerlei Vertragslaufzeiten gibt. Wird eine VM nicht mehr benötigt, kann man diese umgehend runterfahren. Am Monatsende zahlst Du dann nur den Betrag, der bis zu der Abschaltung entstanden ist. Das gibt Dir absolute Flexibilität in beide Richtungen – Du kannst schnell wachsen und, wenn nötig, Dein Setup auch direkt verkleinern.