- stackconf online 2021 | Why you should take care of infrastructure drift
- stackconf online 2021 | On-call done right: how even a developer can help
- stackconf online 2021 | Autoscaling with HashiCorp Nomad
- stackconf online 2021 | Continuous Security – integrating security into your pipelines
- stackconf online 2021 | Kubernetes Native Continuous Deployment with FluxCD, Flagger, and Linkerd
- stackconf online 2021 | Help, My Datacenter is on Fire
- stackconf online 2021 | Continuous Security – Integrating Security into your Pipelines
- stackconf online 2021 | Fuzzing: Finding Your Own Bugs and 0days!
- stackconf online 2021 | Monitoring Microservices The Right Way
- stackconf online 2021 | Policy-as-code in Kubernetes with Gatekeeper
- stackconf online 2021 | Stretching the Service Mesh Beyond the Clouds
- stackconf online 2021 | Stretching the Service Mesh Beyond the Clouds
- stackconf online 2021 | Spot the Anti-Pattern
- stackconf online 2021 | How DevOps changed the way we operate software
- stackconf online 2021 | We accidentally created a Cloud on our IBM Cloud
- stackconf online 2021 | The Tyranny of Taylorism and how to spot Agile BS
- stackconf online 2021 | First hand experience: How Nextcloud stayed productive during COVID-19
- stackconf online 2021 | Reference Architecture for a Cloud Native Digital Enterprise
- stackconf online 2021 | How we finally migrated an eCommerce-Platform to GCP
- stackconf online 2021 | Introducing Thola – A tool for Monitoring and Provisioning Network Devices
- stackconf online 2021 | Setup Min.io and Open Policy Agent for a multi purpose scientific platform
- stackconf online 2021 | GitOps: yea or nay?
- stackconf online 2021 | The Importance of Visuals in Teaching Code and Reducing Bias
- stackconf online 2021 | Enabling multi-cloud and breaking vendor lock-in with Cloud Sidecar
- stackconf online 2021 | Pragmatic App Migration to the Cloud: Quarkus, Kotlin, Hazelcast and GraalVM in action
- stackconf online 2021: Data Driven Security
- stackconf online 2021 | Platform as a Product
stackconf online 2021 is over and was a full success. It was all about open source infrastructure solutions in the spectrum of continuous integration, container, hybrid and cloud technologies. We’re still excited about all of our experts sessions and the large number of participants who joined us from all over the world. In the following you get an insight about one of our talks.
At stackconf online 2021 Matt Jarvis held a talk about the continuous security within pipelines. This is a great topic as security is not only extremly important, but more and more people are realising its importance.
Matt started off by giving us an introduction as to how Dev-ops has progressed and in the pre-cloud era the developer wrote the application and then IT operations took over the security side of things. Nowadays developers write the code, check, deploy and manage almost everything. Which can be a lot! The line has become blurred and the responsibility of security doesn’t have a rightful place, which is where Snyk comes in.
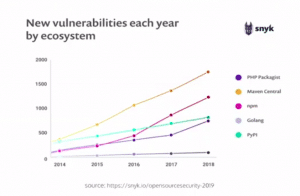
Security is usually considered to be an external practise and as it requires a higher responsibility, it needs to be made easier for developers to use. As we all know, once deployed, it is hard to implement security and having a secure system will help win over the trust of your customers. This problem only grows as each year, more and more code is written, which of course means a higher probability for errors and vunerabilities.
Dependencies and Vunerabilities
The problem with these vunerabilities isn’t always with dependencies themselves, but in fact their dependencies. Up to 70% of the vunerabilities are found here and these indirect dependencies can be used to hide malicious code.
In this example here, the code is hidden in sub dependencies and has had over 440,000 downloads/month! If people are only checking the top layer, there is a whole lot more they are missing. Sometimes all it takes is rebuilding an image or getting newer images. Up to 44% of Docker image vunerabilities can be resolved with a newer base image.
Here lies another problem and that is mainly when it comes to configuring the code. One of the most commonly seen issues is the misconfiguration of code. This is usually unintentional, but also what some developers don’t realise is that not all applications need root access. By default containers run as root and if this rule was changed before it was deployed, it could restrict access for would-be attackers. Something else to consider is the writable file systems that are mounted onto a container. By allowing this an attacker that compromises a container then has write access to the mount drive. If your containers are stateless, the attacker will have a harder time doing damage.
Integrate in a Developers Workflow
Matt went on to talk about how these security flaws can be shifted to the developers level. Security needs to be integrated into a developers workflow to help eliminate these problems at the source. Repositories need to also be taken into consideration and things like two factor authentication, strong key management practises and strong review processes are a great way to reduce weaknesses being exploited.
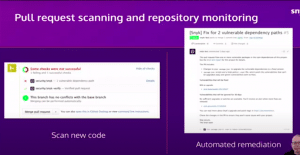
With the help of Snyk a developer is able to identify a lot of these flaws with monitoring scans and checks. These scans and checks can be automated into pipelines and relieve a lot of the responsibility. This was shown in the demo that Matt gave us and with these checks, the vunerabilities were able to be fixed with the Snyk wizard, amazing! This means that errors are found and corrected before they are even deployed. This is what was meant by moving the responsibility back and fixing the problem at the source. By integrating Snyk into the IDE, it fixes issues right away and elimates the need to worry about containers that are already deployed. Snyk is even smart enough to check packages and repos before they are pulled.
This is exactly the right approach to fixing the problem and by making the whole process easier, there really is no reason not to start implementing Snyk in you setups. Matt has identified the problem and shifted the responsibility to developer, but at the same time made it easy to implement. These tools give developers the help they need in order to secure their containers at the source and not cause future problem that can be easily solved with a few checks and corrections. Snyk helps developers at every step on the way and takes care of the security aspect allowing to release code faster and more securely.
Full talk and more from and about stackconf
Watch the the whole talk by Matt Jarvis:
stackconf 2022 will take place in Berlin. The final date will be announced soon. If you want to learn more about infrastructure solutions in advance you have the possibility to take look at our archive where you can find all slides and videos from this year’s stackconf.




















0 Comments